Physical Layer: Modulation
The data rate for the communications link is 2.0Mbps, providing adequate bandwidth for high speed telemetry as well as command and diagnostics. The digital modulation used in the IRIS communications system is Guassian filtered Minimum Shift Keying (GMSK). The bandwidth—bit–time product for the system's Gaussian low pass filter is 0.125. Frequency-Hopping Spread Spectrum (FHSS) is also applied to the carrier. The uplink operates in the Q-V band in the Extremely High Frequency (EHF) spectrum range at 44Ghz. The satellite downlink operates in the Super High Frequency (SHF) spectrum range at 20Ghz. Required bandwidth in both uplink and downlink is 500Mhz.
Frequency Selection
With Ku and Ka bands being mostly saturated [3], there is a shift from centimeter wavelengths to the millimeter bands. For our uplink, we use a 44Ghz EHF carrier frequency and a 20Ghz downlink carrier frequency. This is similar to the currently operational Advanced Extremely High Frequency (AEHF) MILSATCOM system.[4] Since we are not providing communications access to as broad a user-base, IRIS system requires only 500Mhz of bandwidth compared to the 1-2Ghz involved in the AEHS satellites.
Gaussian Minimum Shift Keying
GMSK is a variation of Minimum Shift Keying (MSK). MSK is a continuous phase (CP) Frequency Shift Keying (FSK) modulation scheme where there carrier has no phase discontinuities and frequency shifts occur at the carrier zero crossings. As a CP modulation scheme, the constant-envelope yields high power efficiency, and its independence from amplitude allows for use of class C, non-linear amplifiers. The downside to MSK modulation is its poor power spectral density. With a modulation index of 0.5, where the difference in shift frequencies is one half the data rate, it cannot realize data rates approaching the RF channel bandwidth.
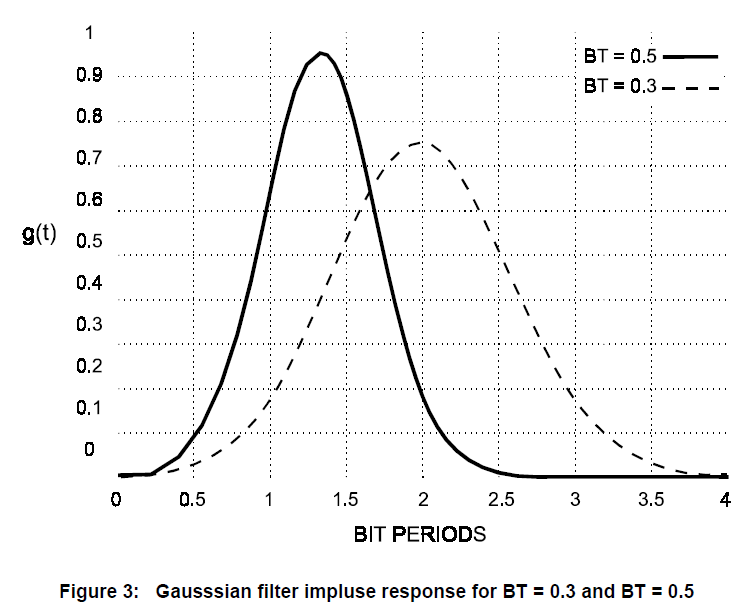
To make the output power spectrum more compact, a premodulation Gaussian low pass filter is applied to the input data impulse train before being applied to the MSK modulation scheme. Figure C3 shows examples of the Gaussian LPF impulse response with respect to a chosen bandwidth—bit–time (BT) product.
The half power cutoff frequency is related to datarate via the following equation:
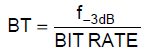
Equation C1. Relationship between channel bitrate, BT product, and channel half power bandwidth. [Figure Reference 3]
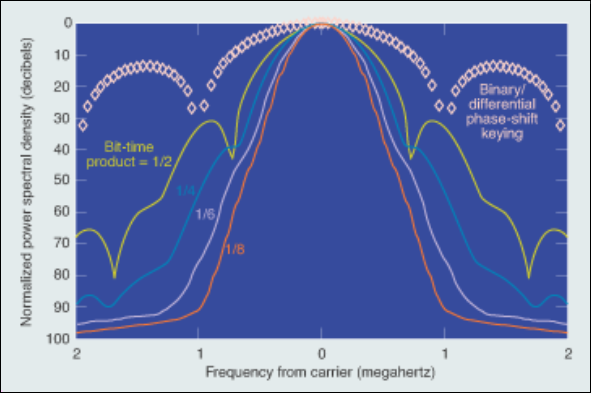
Choosing the BT product is a tradeoff between demodulation complexity and power spectra efficiency. A smaller BT product increases power spectra efficiency with faster rolloff (as seen in Figure C4), but increases demodulation complexity due to greater intersymbol interference (ISI), as seen in the extended bit period in Figure C3. We choose a BT value of 0.125 as there are implementations of demodulators that have been proven to handle the high ISI.
Since the RF bandwidth is controlled by the Gaussian LPF, using Equation C1, our chosen BT value of 0.125, and our target data rate of 2.0Mbps, the -3dB bandwidth for our uncoded GMSK signal is 250kHz.
Despite the increased demodulation complexity, GMSK was chosen because it provides the following advantages:[5]
- Bandwidth efficiency
- Power spectra efficiency
- Independence from power amplifier linearity
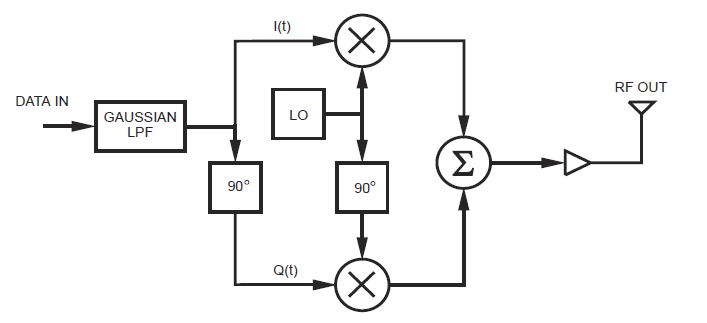
A block diagram for a GMSK coherent modulator is shown in Figure C5.
Frequency-Hopping Spread Spectrum
Spread spectrum techniques provide a protection layer against jamming and interception. The IRIS communications subsystem employs frequency-hopping as its method of spread spectrum. With the improved bandwidth efficiency provided by the GMSK modulation scheme, greater flexibility is provided when hopping the carrier frequency inside of the reserved band. More channels within the reserved band equates to higher chances that the pseudo-random sequence of frequency hops cannot be intercepted. For modulation, the block diagram in Figure C4 need only be modified at the local oscillator to support a frequency hopping scheme.